
You’ve got threats to manage, deadlines to meet, and compliance goals to hit. But how do you know where to start? Our cyber security assessment identifies your gaps and risks, giving you a clear, actionable roadmap so you can move forward with confidence.
Get a FREE One-Off Phishing Email Assessment & Dark Web Scan (Valued at $3,000) when you purchase our service before 31st of October.
request a quote
Cyber Security Consulting Business of the Year Finalist

Years of Expertise
10 Security Analysts, 2 Pen Testers All Australian Based
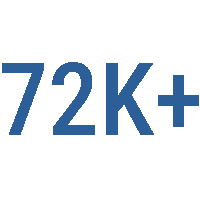
Vulnerabilities Remediated
If you're here, chances are you've been told to "assess your risks" or "get compliant" – but what does that really mean for your business? Many businesses face:
There’s a better way. Instead of guessing and stressing, you need a straightforward roadmap to compliance and security—one that actually works.


Many businesses struggle because their security plans begin in the wrong place. As a trusted cyber security services company, we get you the right assessment from day one, revealing the risks you’re facing, the critical gaps, and the steps needed to address them without wasting time, overspending, or risking compliance failures.
✅ Uncover What’s Putting Your Business at Risk – Identify issues across your systems, users, and third-party relationships.
✅ Prioritise What Matters Most – Not all risks are equal. We help you focus on the gaps that truly need attention.
✅ Stop Wasting Time on Confusing Security Requirements - Know exactly what's required and how to get it done - without endless back and forth.
✅ Keep Your Business Running Smoothly – Stay compliant without unnecessary disruptions or complex security tools.
✅ Keep Your Reputation & Customer Trust – Cyber breaches damage more than your systems – it impacts confidence in your business.
For over 24 years, we’ve helped Australian businesses take control of cyber risks through focused cyber security assessments and practical advice. As a leading cyber security services company, we can do the same for you.

Since our inception, we've stayed ahead of the evolving threat landscape, offering expert cyber security services to keep businesses secure. We’ve built strong relationships with top security vendors and developed in-house solutions to better protect against emerging threats.

Not all Cyber Security Solutions are created equal, and not all offer the same level of protection. Our Cyber Security Services are tailored for businesses with 15+ seats, helping to reduce risks and ensure maximum system uptime but that's just the beginning.
Essential 8 Assessment
Threat and Risk Assessment

cyber security assessments

Identity & Access Security Assessment (IASA)

Cyber Security Vulnerability Assessment (CVA)

Vendor Access Assessment

SharePoint Access Assessment

Password Security Assessment (PSA)
Network Vulnerability Assessment

365/Azure Cyber Assessment

ISO27001 Assessment

Right Fit For Risk (RFFR) Assessment








If you’re based in Sydney or Melbourne and have 15 seats+ that require cyber security support, schedule a meeting with an expert. We’ll ask questions and learn about your cyber security challenges and give you the same advice we give our clients. For enquires by phone: 1300 896 435.
We respect your privacy and promise never to rent or share your details with anybody without your consent.
What are Cyber Security Services, and why is it important for my business?
Cyber Security involves protecting your business's internet-connected systems, including hardware, software, and data, from cyber attacks. Implementing robust Cyber Security services ensure ongoing protection and compliance, preventing data breaches, financial losses, and reputational damage for your business. your business secure in an evolving threat landscape.
What are Cyber Security Services, and why is it important for my business?
Cyber Security involves protecting your business's internet-connected systems, including hardware, software, and data, from cyber attacks. Implementing robust Cyber Security services ensure ongoing protection and compliance, preventing data breaches, financial losses, and reputational damage for your business. your business secure in an evolving threat landscape.
What Cyber Security Services does Emerging IT offer?
Emerging IT provides a comprehensive suite of Cyber Security services, to help protect your business from breaches, downtime and compliance risks.
Our services include:
What Cyber Security Services does Emerging IT offer?
Emerging IT provides a comprehensive suite of Cyber Security services, to help protect your business from breaches, downtime and compliance risks.
Our services include:
How does Emerging IT's approach to Cyber Security differ from other providers?
Emerging IT distinguishes itself through:
How does Emerging IT's approach to Cyber Security differ from other providers?
Emerging IT distinguishes itself through:
How does Emerging IT ensure the confidentiality of my business data?
Emerging IT is committed to safeguarding your data by implementing robust security measures, including encryption, access controls, and continuous monitoring, to prevent unauthorised access and ensure data confidentiality.
How does Emerging IT ensure the confidentiality of my business data?
Emerging IT is committed to safeguarding your data by implementing robust security measures, including encryption, access controls, and continuous monitoring, to prevent unauthorised access and ensure data confidentiality.
What are the benefits of a Cyber Security assessment?
A cyber security assessment helps identify and assess weaknesses in your systems, applications, and networks that could be exploited by cyber criminals. The benefit is twofold: it helps prioritise critical vulnerabilities that need to be fixed immediately and prevents future cyber threats, ultimately protecting your business operations and reputation.
What are the benefits of a Cyber Security assessment?
A cyber security assessment helps identify and assess weaknesses in your systems, applications, and networks that could be exploited by cyber criminals. The benefit is twofold: it helps prioritise critical vulnerabilities that need to be fixed immediately and prevents future cyber threats, ultimately protecting your business operations and reputation.
If you’re based in Sydney or Melbourne and have 15+ seats that require cyber security protection, schedule a meeting with an expert. We’ll discuss your security challenges, assess potential risks, and provide the same expert advice we give our clients.
We manage our career opportunities through external sites. This channel isn’t monitored for recruitment enquiries, so you won’t receive a response here.
Copyright © 2025 Emerging IT