
Has ransomware, phishing, or sophisticated attacks put your reputation at risk? This isn’t just an IT issue—it puts your data in cybercriminals’ hands. Whether it’s a straightforward roadmap or Microsoft 365 breach protection, strengthen your defences and secure your business fast.
Get a FREE One-Off Phishing Email Assessment & Dark Web Scan (Valued at $3,000) when you purchase our service before 31st of September.
Request a quote
Cyber Security Consulting Business of the Year Finalist

Years of Expertise
10 Security Analysts, 2 Pen Testers All Australian Based
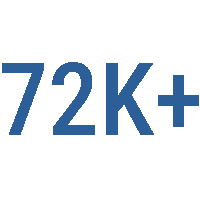
Vulnerabilities Remediated
If you're here, chances are you want to "get protected" - but what does that actually mean for your business? Many businesses face:
There’s a better way. Instead of guesswork and stress, you need a straightforward roadmap to compliance and security—one that actually works.


Cyber security isn’t just IT setup—it’s protecting your business from Microsoft 365 data breaches and evolving threats. Many companies assume their security is covered, only to find out too late. As a trusted Cyber Security Services provider, we help businesses like yours get secure fast, without the risk of breaches or costly mistakes.
✅ Close Gaps in Microsoft 365 Security – Don’t assume your Microsoft 365 breach protection is sufficient. Address vulnerabilities like weak passwords and outdated authentication methods.
✅ Prevent Costly Office 365 Security Breaches – Cybercriminals exploit overlooked gaps in your security. Get tailored solutions to ensure your business stays protected against phishing, ransomware, and other threats.
✅ Stop Wasting Time on Guesswork – Understand exactly where your security is lacking and get a clear roadmap to address gaps like MFA enforcement and real-time alerts to avoid an Office 365 data breach.
✅ Ensure Seamless, Ongoing Protection – Stay secure without disruptions. Get continuous monitoring and visibility into your Microsoft 365 environment, making unauthorised access easy to spot before it's too late.
✅ Protect Your Reputation & Customer Trust – A Microsoft 365 data breach doesn’t just affect your systems; it erodes trust in your business. Build a strong security foundation to keep your business and clients safe.
For over 24 years, we’ve helped Australian businesses achieve compliance and stronger security—without the usual frustration. As a leading cyber security services company, we can do the same for you.

Since our inception, we've stayed ahead of the evolving threat landscape, offering expert cyber security services to keep businesses secure. We’ve built strong relationships with top security vendors and developed in-house solutions to better protect against emerging threats.

Not all Cyber Security Solutions are created equal, and not all offer the same level of protection. Our Cyber Security Services are tailored for businesses with 15+ seats, helping to reduce risks and ensure maximum system uptime but that's just the beginning.
it support & maintenance
microsoft 365 breach protection

cyber security assessments

Essential 8 framework alignment

governance & compliance (ISO 27001, RFFR, GDPR)

Vulnerability & remediation service

Security Awareness Training

penetration testing
A single Microsoft 365 breach costs Australian businesses an average of $276,000 in downtime, legal costs, recovery, and loss of trust (ACSC Annual Cyber Threat Report 2022–23).
per Microsoft 365 tenant
per Microsoft 365 tenant








If you’re based in Sydney or Melbourne and have 15 seats+ that require cyber security support, schedule a meeting with an expert. We’ll ask questions and learn about your cyber security challenges and give you the same advice we give our clients.
We respect your privacy and promise never to rent or share your details with anybody without your consent.
What are Cyber security Services, and Why Is It Important for My Business?
Cyber security services protect your business’s internet-connected systems, including hardware, software, and data, from cyber attacks. Implementing robust cyber security services ensures ongoing protection, compliance, and prevents data breaches, financial losses, and reputational damage.
What are Cyber security Services, and Why Is It Important for My Business?
Cyber security services protect your business’s internet-connected systems, including hardware, software, and data, from cyber attacks. Implementing robust cyber security services ensures ongoing protection, compliance, and prevents data breaches, financial losses, and reputational damage.
What Cyber security Services Does Emerging IT Offer?
Emerging IT provides a comprehensive suite of cyber security services to protect your business from breaches, downtime, and compliance risks. Our services include:
Cyber security assessments
Microsoft 365 breach protection
Endpoint protection and patching
Email and web filtering
Penetration testing
Essential 8 uplift programs
ISO 27001 and GDPR support
Right Fit For Risk advisory
Security awareness training
Governance and compliance planning
Vulnerability assessments and remediation
What Cyber security Services Does Emerging IT Offer?
Emerging IT provides a comprehensive suite of cyber security services to protect your business from breaches, downtime, and compliance risks. Our services include:
Cyber security assessments
Microsoft 365 breach protection
Endpoint protection and patching
Email and web filtering
Penetration testing
Essential 8 uplift programs
ISO 27001 and GDPR support
Right Fit For Risk advisory
Security awareness training
Governance and compliance planning
Vulnerability assessments and remediation
How Does Emerging IT’s Approach to Cyber security Differ from Other Providers?
Emerging IT stands out by offering:
Tailored Solutions: We work closely with you to create customised cybersecurity strategies that align with your business goals.
Proactive Measures: Our team continuously updates methodologies and tools to stay ahead of emerging threats.
Comprehensive Support: From initial assessments to ongoing management, we offer end-to-end cyber security services.
Local Support: Based in Melbourne and Sydney, our teams provide local support with a deep understanding of the Australian business environment and threat landscape.
How Does Emerging IT’s Approach to Cyber security Differ from Other Providers?
Emerging IT stands out by offering:
Tailored Solutions: We work closely with you to create customised cybersecurity strategies that align with your business goals.
Proactive Measures: Our team continuously updates methodologies and tools to stay ahead of emerging threats.
Comprehensive Support: From initial assessments to ongoing management, we offer end-to-end cyber security services.
Local Support: Based in Melbourne and Sydney, our teams provide local support with a deep understanding of the Australian business environment and threat landscape.
What Is 365 Cloud Secure?
365 Cloud Secure is a fully managed cyber security service designed to protect your Microsoft 365 environment. It monitors for identity threats, hardens your setup, and provides fast response to stop breaches.
What Is 365 Cloud Secure?
365 Cloud Secure is a fully managed cyber security service designed to protect your Microsoft 365 environment. It monitors for identity threats, hardens your setup, and provides fast response to stop breaches.
Isn’t Microsoft 365 Already Secure?
Not by default. Microsoft provides the tools, but it’s up to you to configure and monitor them. Many businesses leave key features like Multi-Factor Authentication (MFA), alerting, and access control either misconfigured or completely off.
Isn’t Microsoft 365 Already Secure?
Not by default. Microsoft provides the tools, but it’s up to you to configure and monitor them. Many businesses leave key features like Multi-Factor Authentication (MFA), alerting, and access control either misconfigured or completely off.
How Does 365 Cloud Secure Differ from My MSP?
While MSPs focus on IT support and infrastructure, 365 Cloud Secure replaces your MSP with a dedicated cyber security first team that prevents breaches, hardens security, and ensures compliance.
How Does 365 Cloud Secure Differ from My MSP?
While MSPs focus on IT support and infrastructure, 365 Cloud Secure replaces your MSP with a dedicated cyber security first team that prevents breaches, hardens security, and ensures compliance.
What Types of Threats Does 365 Cloud Secure Detect and Stop?
We monitor for suspicious logins, MFA token theft, risky behaviour, admin abuse, and more. If something happens, we alert and act quickly to contain the threat before it spreads.
What Types of Threats Does 365 Cloud Secure Detect and Stop?
We monitor for suspicious logins, MFA token theft, risky behaviour, admin abuse, and more. If something happens, we alert and act quickly to contain the threat before it spreads.
Is remediation included in the Microsoft 365 uplift?
Every business is different. Remediation is not included in the monthly fee because each organisation has a different level of risk and security debt. You’ll get a clear report, and can choose to fix everything at once or spread it out over time.
Is remediation included in the Microsoft 365 uplift?
Every business is different. Remediation is not included in the monthly fee because each organisation has a different level of risk and security debt. You’ll get a clear report, and can choose to fix everything at once or spread it out over time.
How does Emerging IT ensure the confidentiality of my business data?
Emerging IT is committed to safeguarding your data by implementing robust security measures, including encryption, access controls, and continuous monitoring, to prevent unauthorised access and ensure data confidentiality.
How does Emerging IT ensure the confidentiality of my business data?
Emerging IT is committed to safeguarding your data by implementing robust security measures, including encryption, access controls, and continuous monitoring, to prevent unauthorised access and ensure data confidentiality.
If you’re based in Sydney or Melbourne and have 15+ seats that require cyber security protection, schedule a meeting with an expert. We’ll discuss your security challenges, assess potential risks, and provide the same expert advice we give our clients.
We manage our career opportunities through external sites. This channel isn’t monitored for recruitment enquiries, so you won’t receive a response here.Copyright © 2025 Emerging IT