
Overwhelmed by threats, standards, and to-do lists? Whether it’s internal network penetration testing or external web app scans, we give you a clear roadmap — keeping you compliant and free from hidden risks.
request a quote
Cyber Security Consulting Business of the Year Finalist

Years of Expertise
10 Security Analysts, 2 Pen Testers All Australian Based
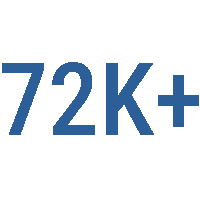
Vulnerabilities Remediated
If you're here, chances are you've been told to "tighten your security or get your regular pentesting completed" — but what does that actually mean for your business?
There’s a better way. Instead of guesswork and stress, you need a straightforward compliant roadmap - one built on certified cybersecurity penetration testing that actually works.


Penetration testing doesn’t come with a step-by-step guide — but that’s where we come in. As a trusted provider of cybersecurity penetration testing, we help businesses uncover hidden risks, meet compliance standards, and strengthen security without delays, confusion, or bloated costs.
✅ Get Audit Ready Fast – Whether you need Essential Eight, ISO 27001, or PCI compliance, our internal and external penetration testing helps you tick the right boxes with confidence.
✅ Avoid Costly Breaches & Fines – Close security vulnerabilities before they turn into expensive incidents with tailored pen testing tools.
✅ No Risk to Operations – Testing is designed to be thorough, non-disruptive, and risk-aligned to your business profile.
✅ Strengthen Customer & Partner Trust – Demonstrate you're proactive with security a key factor in winning and keeping contracts, clients, and credibility.
For over 24 years, we’ve helped Australian businesses strengthen their security posture through clear, certified, and actionable penetration testing services. We can help you do the same.

Since our inception, we've stayed ahead of the evolving threat landscape, offering expert cyber security services to keep businesses secure. We’ve built strong relationships with top security vendors and developed in-house solutions to better protect against emerging threats.

Not all Cyber Security Solutions are created equal, and not all offer the same level of protection. Our Cyber Security Services are tailored for businesses with 15+ seats, helping to reduce risks and ensure maximum system uptime but that's just the beginning.

External Penetration Test

Social Engineering Penetration Test

Internal Penetration Test

Wireless Penetration Test

Web Application Penetration Test
Workstation Penetration Test

Web Services Penetration Test
Custom Penetration Test








If you’re based in Sydney or Melbourne and have 15 seats+ that require cyber security support, schedule a meeting with an expert. We’ll ask questions and learn about your cyber security challenges and give you the same advice we give our clients.
We respect your privacy and promise never to rent or share your details with anybody without your consent.
What are Cyber Security Services, and why is it important for my business?
Cyber Security involves protecting your business's internet-connected systems, including hardware, software, and data, from cyber attacks. Implementing robust Cyber Security services ensure ongoing protection and compliance, preventing data breaches, financial losses, and reputational damage for your business. your business secure in an evolving threat landscape.
What are Cyber Security Services, and why is it important for my business?
Cyber Security involves protecting your business's internet-connected systems, including hardware, software, and data, from cyber attacks. Implementing robust Cyber Security services ensure ongoing protection and compliance, preventing data breaches, financial losses, and reputational damage for your business. your business secure in an evolving threat landscape.
What Cyber Security Services does Emerging IT offer?
Emerging IT provides a comprehensive suite of Cyber Security services, to help protect your business from breaches, downtime and compliance risks.
Our services include:
What Cyber Security Services does Emerging IT offer?
Emerging IT provides a comprehensive suite of Cyber Security services, to help protect your business from breaches, downtime and compliance risks.
Our services include:
How does Emerging IT's approach to Cyber Security differ from other providers?
Emerging IT distinguishes itself through:
How does Emerging IT's approach to Cyber Security differ from other providers?
Emerging IT distinguishes itself through:
How does Emerging IT ensure the confidentiality of my business data?
Emerging IT is committed to safeguarding your data by implementing robust security measures, including encryption, access controls, and continuous monitoring, to prevent unauthorised access and ensure data confidentiality.
How does Emerging IT ensure the confidentiality of my business data?
Emerging IT is committed to safeguarding your data by implementing robust security measures, including encryption, access controls, and continuous monitoring, to prevent unauthorised access and ensure data confidentiality.
What is Penetration Testing , and how does Emerging IT assist with it?
Penetration testing is a simulated cyber attack used to identify vulnerabilities before real hackers can exploit them.
Emerging IT specialises in internal, external, and web application penetration testing tailored to your risk profile.
Our certified Australian team helps you meet compliance requirements like ISO 27001 and Essential Eight. We uncover hidden risks and provide clear, actionable insights to keep your business secure and audit-ready.
What is Penetration Testing , and how does Emerging IT assist with it?
Penetration testing is a simulated cyber attack used to identify vulnerabilities before real hackers can exploit them.
Emerging IT specialises in internal, external, and web application penetration testing tailored to your risk profile.
Our certified Australian team helps you meet compliance requirements like ISO 27001 and Essential Eight. We uncover hidden risks and provide clear, actionable insights to keep your business secure and audit-ready.
If you’re based in Sydney or Melbourne and have 15+ seats that require cyber security protection, schedule a meeting with an expert. We’ll discuss your security challenges, assess potential risks, and provide the same expert advice we give our clients.
We manage our career opportunities through external sites. This channel isn’t monitored for recruitment enquiries, so you won’t receive a response here.Copyright © 2025 Emerging IT