
You have gaps to fix, deadlines to meet, and managing cyber threats - but where do you start? Whether it's Essential 8 or ISO 27001, get a straight forward roadmap that removes the guesswork and gets you compliant fast.
Schedule a Discovery Call
Cyber Security Consulting Business of the Year Finalist

Years of Expertise
10 Security Analysts, 2 Pen Testers All Australian Based
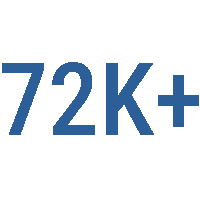
Vulnerabilities Remediated
The attacks are getting smarter. The regulators are stepping in. The headlines are becoming business risks.
This is no longer just an IT issue. It’s a business risk that affects compliance, reputation, and revenue.
READ THE BLOG POST - Cyber Security Failures Are No Longer an Option for Financial Services


If your cyber program isn’t up to scratch, you risk:
Data theft – client records, financial data, login credentials
Regulator action – ASIC is actively pursuing firms with security gaps
Reputation damage – trust takes years to build and seconds to lose
Loss of revenue and clients – clients leave after breaches
Insurance blowback – higher premiums or denied claims after an incident
Cyber breaches hit more than your systems. They hit the confidence of clients, investors and your team.
For over 24 years, we’ve helped Australian businesses achieve compliance and stronger security—without the usual frustration. As a leading cyber security services company, we can do the same for you.
DOWNLOAD THE CHECKLIST - The Financial Services Cyber Security Checklist

Since our inception, we've stayed ahead of the evolving threat landscape, offering expert cyber security services to keep businesses secure. We’ve built strong relationships with top security vendors and developed in-house solutions to better protect against emerging threats.

Not all Cyber Security Solutions are created equal, and not all offer the same level of protection. Our Cyber Security Services are tailored for businesses with 15+ seats, helping to reduce risks and ensure maximum system uptime but that's just the beginning.
it support & maintenance
microsoft 365 breach protection

cyber security assessments

Essential 8 framework alignment

governance & compliance (ISO 27001, RFFR, GDPR)

Vulnerability & remediation service

Security Awareness Training

penetration testing
Lorem ipsum dolore
per Microsoft 365 tenant
per Microsoft 365 tenant
per Microsoft 365 tenant








If you’re based in Sydney or Melbourne and have 15 seats+ that require cyber security support, schedule a meeting with an expert. We’ll ask questions and learn about your cyber security challenges and give you the same advice we give our clients.
We respect your privacy and promise never to rent or share your details with anybody without your consent.
What are Cyber Security Services, and why is it important for my business?
Cyber Security involves protecting your business's internet-connected systems, including hardware, software, and data, from cyber attacks. Implementing robust Cyber Security services ensure ongoing protection and compliance, preventing data breaches, financial losses, and reputational damage for your business. your business secure in an evolving threat landscape.
What are Cyber Security Services, and why is it important for my business?
Cyber Security involves protecting your business's internet-connected systems, including hardware, software, and data, from cyber attacks. Implementing robust Cyber Security services ensure ongoing protection and compliance, preventing data breaches, financial losses, and reputational damage for your business. your business secure in an evolving threat landscape.
What Cyber Security Services does Emerging IT offer?
Emerging IT provides a comprehensive suite of Cyber Security services, to help protect your business from breaches, downtime and compliance risks.
Our services include:
What Cyber Security Services does Emerging IT offer?
Emerging IT provides a comprehensive suite of Cyber Security services, to help protect your business from breaches, downtime and compliance risks.
Our services include:
How does Emerging IT's approach to Cyber Security differ from other providers?
Emerging IT distinguishes itself through:
How does Emerging IT's approach to Cyber Security differ from other providers?
Emerging IT distinguishes itself through:
How does Emerging IT ensure the confidentiality of my business data?
Emerging IT is committed to safeguarding your data by implementing robust security measures, including encryption, access controls, and continuous monitoring, to prevent unauthorised access and ensure data confidentiality.
How does Emerging IT ensure the confidentiality of my business data?
Emerging IT is committed to safeguarding your data by implementing robust security measures, including encryption, access controls, and continuous monitoring, to prevent unauthorised access and ensure data confidentiality.
What is the Essential 8 framework, and how does Emerging IT align with it?
The Essential 8 is a set of strategies developed by the Australian Cyber Security Centre to mitigate cyber security incidents. Emerging IT assists organisations in aligning with these strategies to strengthen their overall security posture.
What is the Essential 8 framework, and how does Emerging IT align with it?
The Essential 8 is a set of strategies developed by the Australian Cyber Security Centre to mitigate cyber security incidents. Emerging IT assists organisations in aligning with these strategies to strengthen their overall security posture.
If you’re based in Sydney or Melbourne and have 15+ seats that require cyber security protection, schedule a meeting with an expert. We’ll discuss your security challenges, assess potential risks, and provide the same expert advice we give our clients.
If you're interested in a job, please visit our website
Copyright © 2026 Emerging IT